See meetod töötab juhul, kui sul on võimalus pilti üles laadida, näiteks füüsilistes masinates või spetsiaalsetes serverites IPMI või ILO moodulite kaudu. Kui sul on virtuaalne server, palun võta meiega ühendust, esitades tugipileti.
Kui on ebaõnnestunud parooli sisestamise katsed, võib Windowsi konto lukustuda.
Kui puutud selle probleemiga kokku, pead laadima systemrescue.iso pildi. Selle pildi saad alla laadida järgmiselt lingilt: https://www.system-rescue.org/Download/.
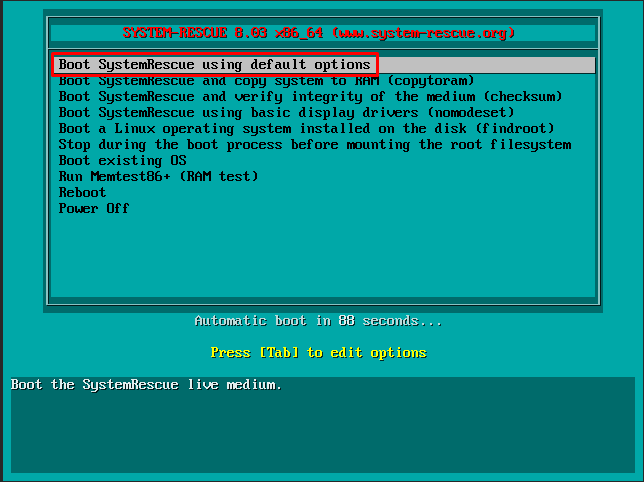
Pärast pildi allalaadimist tuleb süsteem taaskäivitada ja sellest buutida.
Valige “Boot SystemRescue using default options.”
Sisesta käsk fdisk -l | more, et vaadata kettajaotusi. Meie juhul asub Windowsi operatsioonisüsteem partitsioonil vda2. Kontrolli käsuga lsblk, kas pildifailid ei ole sellele partitsioonile ühendatud.
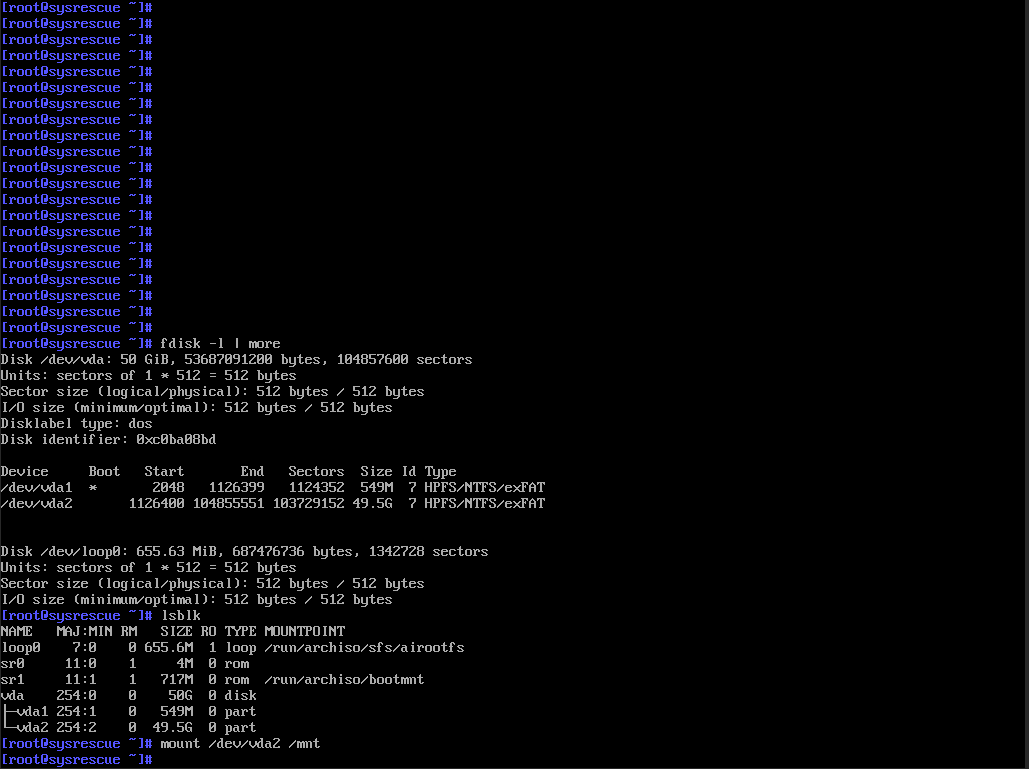
Sellisel juhul ei ole partitsioonil vda2 ühtegi ühenduspunkti. Seega ühendame selle. Sisestame käsu mount /dev/vda2 /mnt
/mnt on koht, kuhu paigaldatakse SystemRescueCD failid.
Kui SystemRescueCD failid on juba ühendatud, ühenda need lahti käsuga umount /mnt. Seejärel käivita käsk mount /dev/vda2 /mnt.
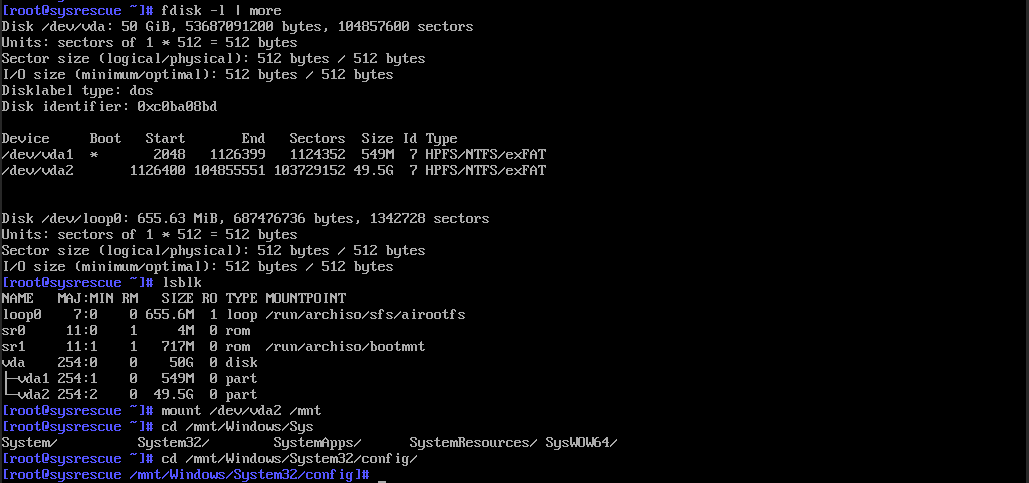
Järgmisena sisesta käsk cd /mnt/Windows/System32/config/.
Nüüd sisesta käsk chntpw -i SAM.
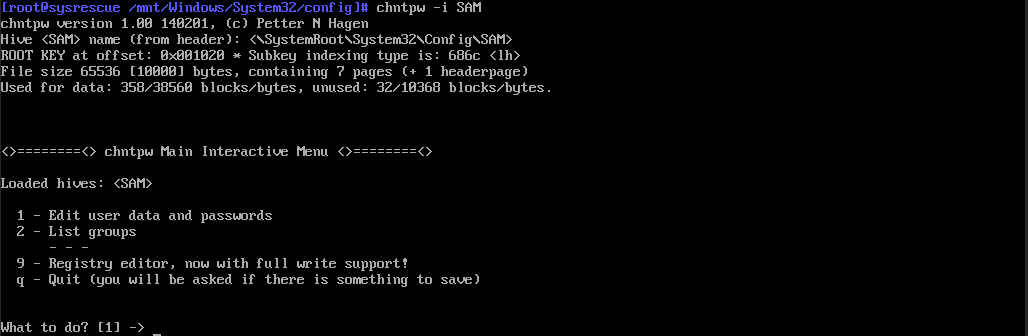
Seejärel vajuta number '1', et muuta kasutaja andmeid.
Sa näed, et administraatori kasutaja on lukustatud, mida näitab kirje "dis/lock."
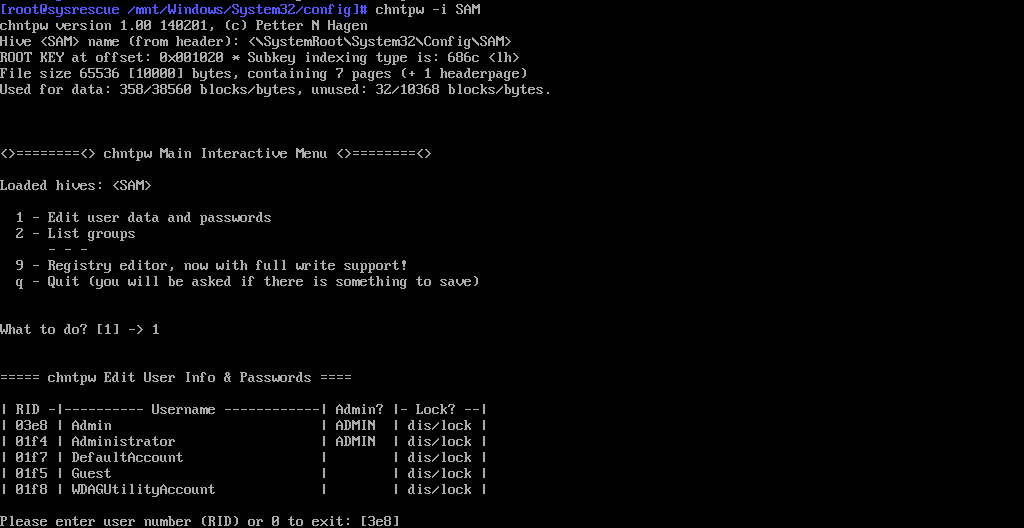
Sisesta RID number. Esiotsa olev '0' on valikuline. Meie puhul on see "1f4."
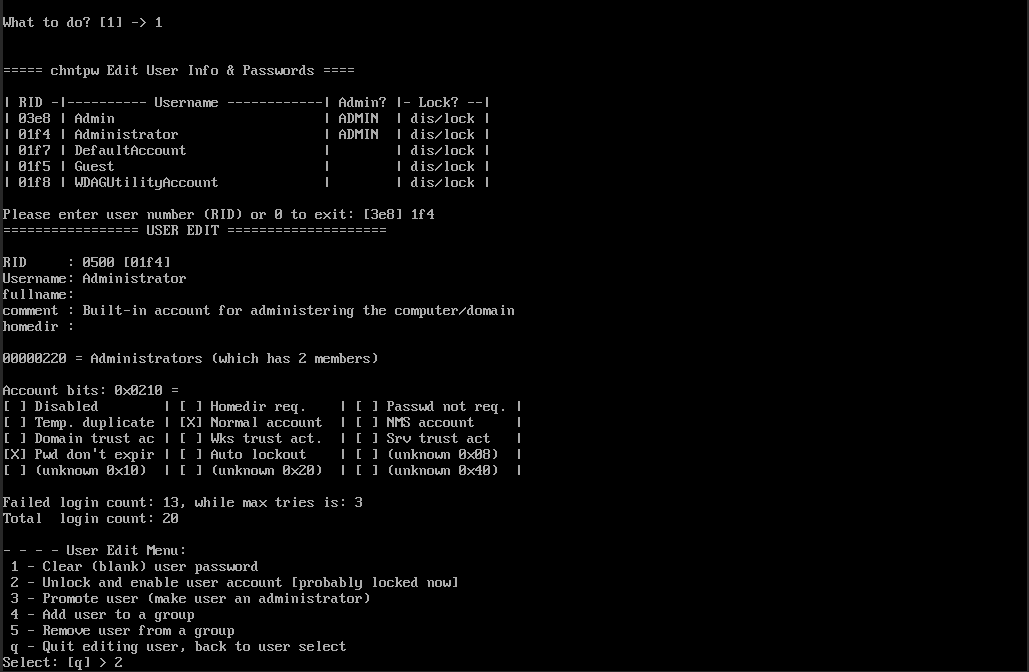
Kasutaja valitakse. Konto avamiseks sisesta '2'.
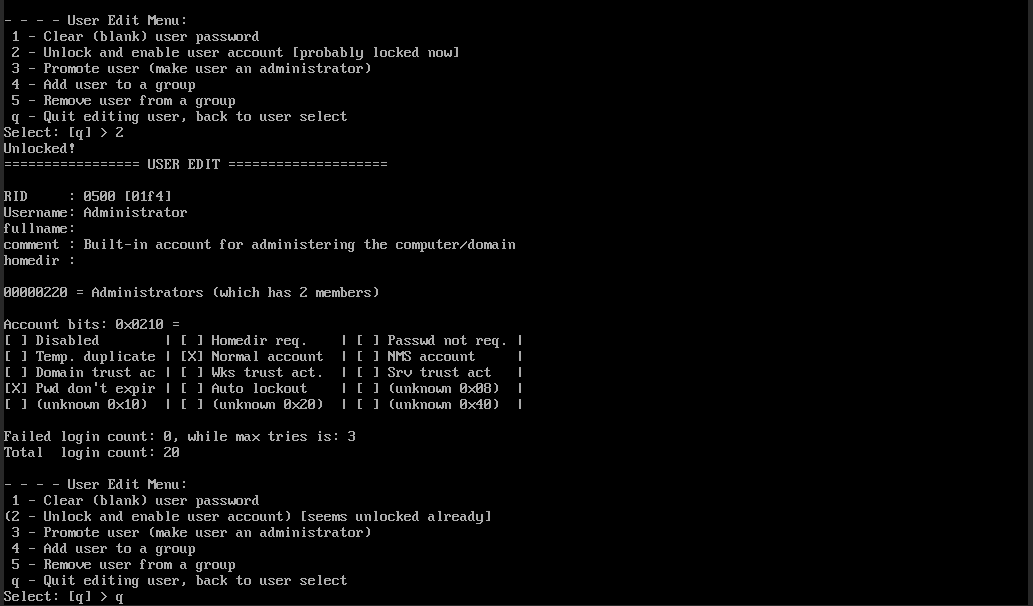
Konto avatakse. Nüüd kirjuta kaks korda 'q', et väljuda, ja seejärel sisesta 'y'.
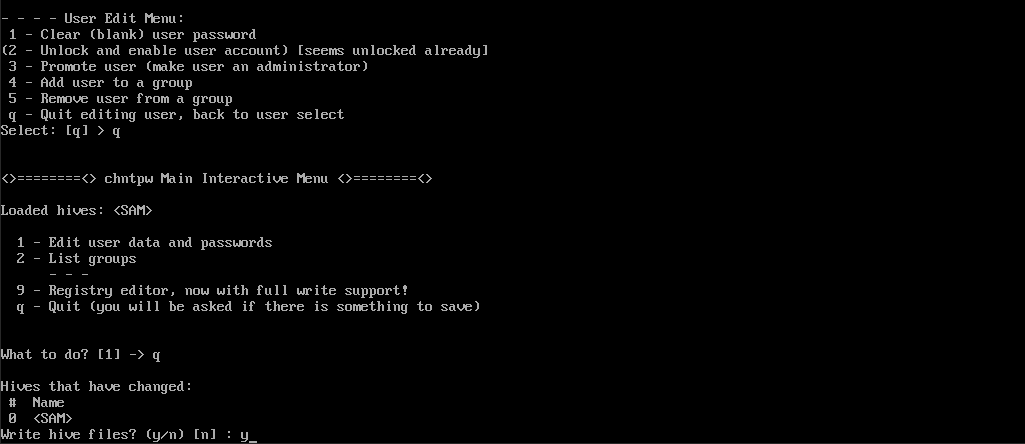
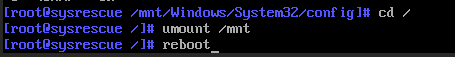
Seejärel minge juurkataloogi: cd /
Sisesta käsk umount /mnt.
Sisesta käsk reboot, et süsteem taaskäivitada.
Pärast taaskäivitust saad sisse logida varasemalt lukustatud kasutajakontoga.







